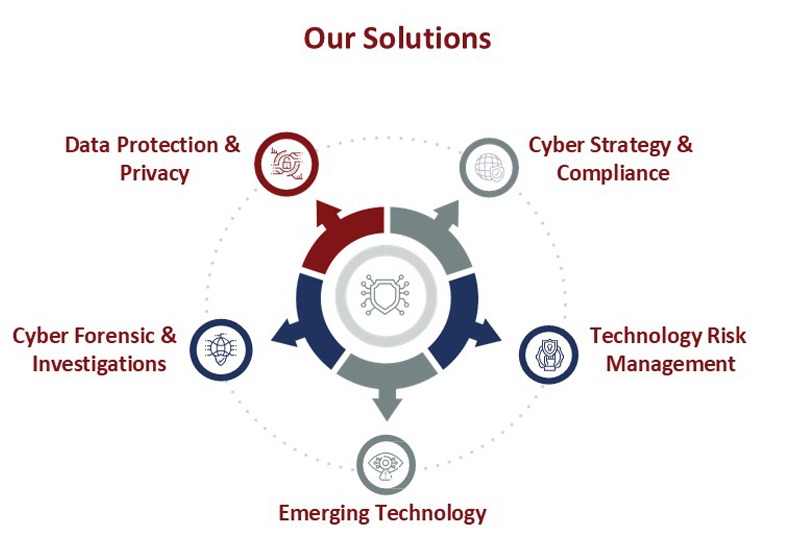
Every business, regardless of its size, faces the potential threat of a cyber attack. This is because every business, along with its vendors, partners, customers, and other stakeholders, possesses key assets that criminals may seek to exploit. These assets could be monetary funds, financial data, personal information of employees and customers, or even the infrastructure that supports the business.
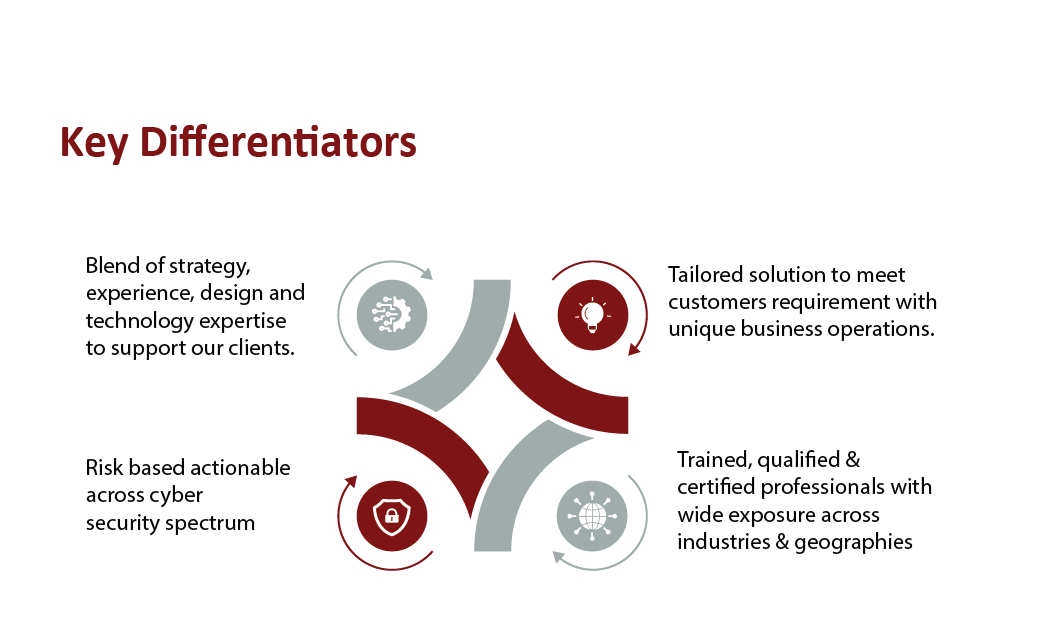
The approach and commitment of organizations to implementing cyber and information security are pivotal in minimizing risks and aligning with their business objectives. Our unique business model, values, and approach, coupled with our well-trained and highly skilled workforce, provide deep insight and trustworthy consultation to clients seeking a reliable partner. Our Cyber Security team comprises professionals with a unique blend of technological expertise and business acumen derived from diverse backgrounds and extensive experience in various industries and sectors.